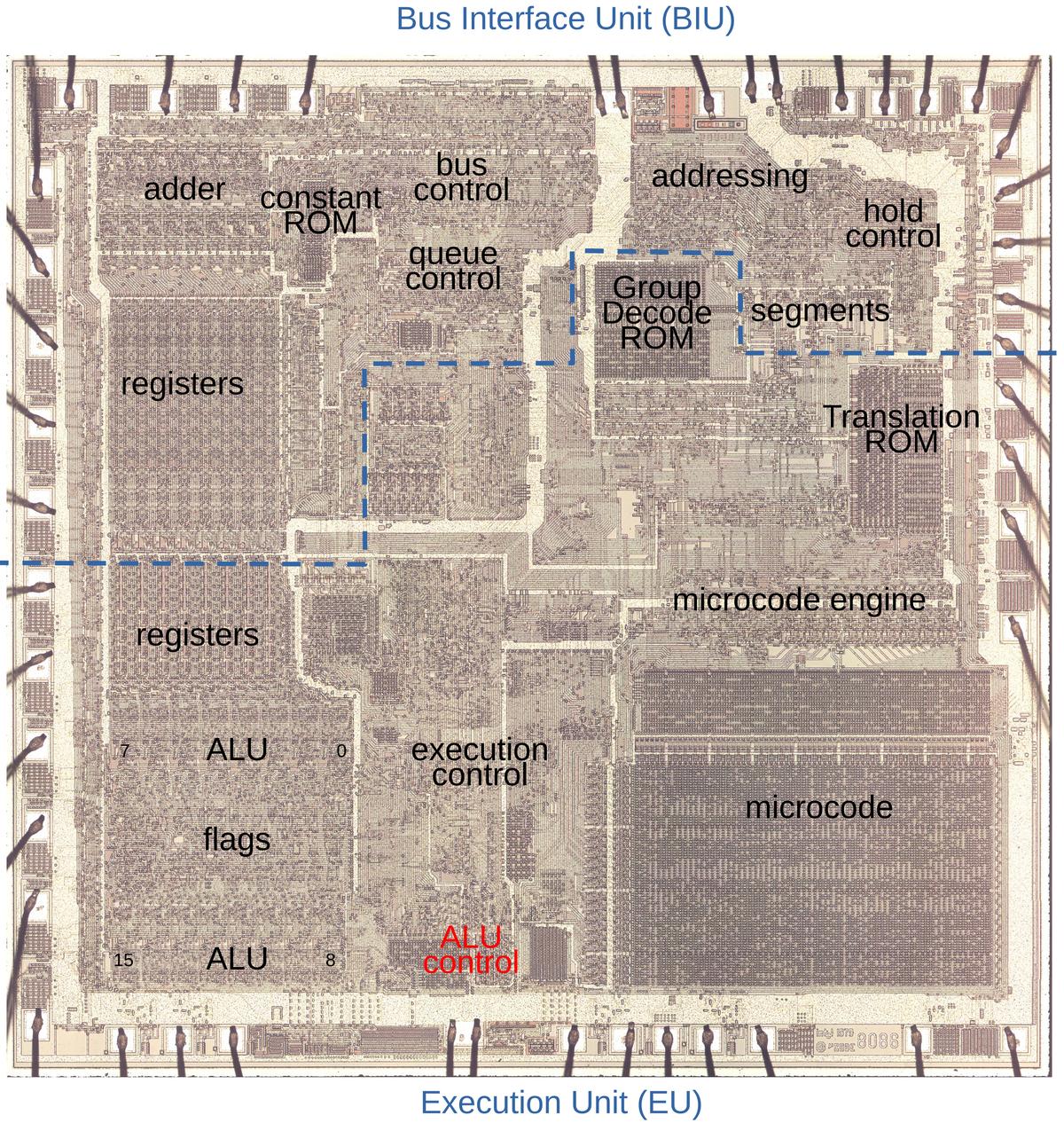
Osebna arheologija Roga
Ljubljanskemu kiču je kljubovalo kar nekaj vročih točk v posredni in neposredni bližini mestnega središča. Poleg pisane druščine na Kongresnem trgu, pri Cukrarni, Metelkovi in Šumiju je – še posebej po svetovnem finančnem zlomu nesposobnih bank in skladov – kolo antikapitalizma vodila veličastna umazanija za zidom na Trubarjevi ulici. Zdaj uglajena fasada je bila takrat vsa porisana, zdaj popeglana notranjost pa je bila polna kreativnih snovi, ki se jih prav nihče tam notri ni bal. Ravno nasprotno. Spomnim se trenutka, ko sem odkrila Rog. Bila je zima leta 2008 in vedoželjno sem se iztrgala iz udobja Rožne doline, da bi se sprehodila po prazničnem mestnem središču. Ljubljana leta 2008 še ni bila predmet množičnega butičnega turizma, bila je še neznana nova Evropa. Edina skupina tujcev je bila pravzaprav res fina druščina Američanov, tu živečih že več let, ki so imeli slovenske partnerice, otroke in službe. Kakorkoli, sprehod po praznični Ljubljani tistega leta v ničemer ni bil svetovljanski, pravzaprav je bil rahlo odtujen, saj so se čez Prešernov trg premikale trume prijateljev ali so čezenj drseli parčki – vsak namenjen proti nekemu konkretnemu cilju. Hitro so se izmikali svetlobi lučk ter izginjali v odprta usta takrat še ne tako požrešnih lokalov. Tu in tam je bilo videti nekaj tujcev, ki so prišli praznovat svoj prosti čas v mesto, a po večini je šlo za študente iz programa Erasmus, prijatelje, ki so se spoznali na izmenjavi ter se vsako leto srečevali v domačem mestu enega iz skupine. Za Balkance je še vedno veljal strožji vizumski režim, zato ni bilo slišati toliko jugoslovanščine, razen v nekaterih lokalih in prehranskih obratih, kot to narekuje trebuh, ki išče kruh – in to na obeh straneh šanka.
Skratka, gledati te vesele, zimsko opravljene ljudi, ki hitijo po opravkih, utegne postati turobno, kajti zdi se, da so vsi kam namenjeni v okviru zaključenega dejstva in predvsem zaključene družbe. Težko se je seznaniti z ljudmi, če je druženje zaključeno: če se jim mudi na že dogovorjeno lokacijo, na zabavo za zaprtimi vrati, še posebej, če je namenjena tistim z debelimi denarnicami. Tako je moje izurjeno oko sčasoma vse laže prepoznavalo tipe ljudi, odnosov, načinov druženja in pričakovanj družbe – že po hitrosti in načinu hoje, telesni drži, šele nato po obleki in govorjenih jezikih sem prepoznavala arhetipe, izvirnike, plagiate, ponavljanje, ponavljanje s spremembo. Izurjeno oko je bilo nazadnje v delcu sekunde sposobno približno oceniti, komu se kam mudi, kdo je ali bo kmalu skupaj, ali se je sprl, ali »se ga bo s tem ali onim nocoj ubil«, ali gredo sodelavci, znanci ali prijatelji kam ali le h komu domov, morda v kafič in ali se kakemu posamezniku ali posameznici obeta dober večer. V vseh navedenih situacijah je k ljudem zaradi narave prostora, ki ga zasedajo – osebnega ali privatiziranega – težko pristopiti; in to ne le kot tujec, neznanec, temveč tudi kot sopotnik, someščan. Zato se jasno spomnim in nikoli ne bom pozabila, kako je moje oko v bežnem trenutku, v hipu zaznalo nekoga, ki je izstopal iz trume hitečih zaključenih družb in drvečih posameznikov. S Tromostovja je nekako pritavala silhueta moškega s temno kapuco in pivom v roki, ki se je v povsem drugačnem – zmernem – ritmu mimo vseh dokaj odločno pomikal proti temni uličici, nekam za spomenik. Vstala sem in mu – brez kančka dvoma – sledila tja, kamor je odhlačal. Hodil je in bil videti preprosto in sproščeno, kar je kazalo, da se giblje proti sproščenemu okolju. Deloval je zamišljeno, kar je dalo misliti, da ni namenjen na zmenek ali v glasno in razposajeno druščino, hkrati pa ni bil videti, kot da gre h komu domov, saj je imel v roki odprto pivo. Ura ni bila ravno pozna, a noč je že zajela mesto, in medtem ko so se lučke na trgu v ozadju še svetile, sva midva, oddaljena nekaj korakov, drug za drugim izginjala v temo nečesa, kar se je takrat zdelo kot neskončno dolga in ozka ulica. Nisem vedela, kam grem niti komu sledim, a to ni bilo pomembno, saj sem imela zanesljiv občutek, da bom nekaj odkrila, in res: po razmeroma dolgi hoji, kot se je zdelo takrat, je v nekem trenutku moj nevedni nočni vodič švignil za neka ozka vrata ob podolgovatem zidu in izginil v mrak. Takoj za njim sem brez pretiranega razmišljanja skozi vrata švignila še sama; prej se mi je tista ozka uličica zdela temna, za steno pa me je zajela ena sama črnina. Ni treba posebej poudarjati, da sem že takoj izgubila skrivnostnega mladeniča s kapuco in tako obstala na dvorišču med nekimi hiškami in ogromno, temno, na videz zapuščeno stavbo. Prijetno presenečena nad to mondeno, svetovljansko strukturo, ki vabi k raziskovanju svojih kotičkov, sem se odpravila – kakopak – raziskovat in šla skozi prva vrata, ki sem jih zagledala. V eni sobi je stalo kolo, v drugi je bil WC, v tretji je skupina moških srednjih let gledala nogomet in pila pivo. Prisedla sem k njim, vsi so me pogledali in razen kretnje proti paleti, češ da si lahko tudi jaz vzamem pivo, nihče ni rekel popolnoma nič. Ko pa je bilo tekme konec, kar je bilo kmalu po mojem prihodu, sem se zahvalila, pozdravila in šla naprej.
Na dvorišču sem slišala nekaj ljudi, ki so govorili špansko, in pod bledo mesečino zaznala, kako hitro korakajo nekam v zadnjo, najimpozantnejšo izmed stavb – pa sem jim nemudoma sledila. Šli smo skozi večja pločevinasta vrata, zatem po stopnicah na levo in za še ena, malo težja vrata, za katerimi se je pred menoj razprl pisan prostor s čudnimi in prikupnimi umetninami, neko folk-pank zvočno kuliso ter plešočimi ljudmi. Uživala sem. Plesala sem sama s seboj, a hkrati obkrožena z ljudmi, ki so uživali v istem zvoku in »vajbu«, vedoč, da na tem mestu, če tako želim, dejansko lahko te ljudi tudi spoznam. Nato sem še malo opazovala okolje in veselje ter na neki točki zadovoljna odšla z mislijo, da se ob prvi priložnosti spet vrnem. Tako je tudi bilo. Kot tiha udeleženka sem se vedno vračala in pogosto zahajala v staro tovarno, kjer sem opazovala dogajanje in se vedno znova ujela v misli, da je to pač ta svetovljanskost. Kako super je, da imaš v mestu prostor samote, družbe, spontanosti, enakosti, naključij; ki mu ni mar, da je umazan, v katerem ni treba, da je vse novo in drago – niti plačljivo ne; in kjer lahko vsak vadi in se uri v različnih veščinah, si premisli, sam nekaj zažene ter se srečuje s popotniki in sorodnimi dušami – po koordinatah in po etičnih ter političnih prepričanjih. Tu, v kompleksu stare tovarne, za tem dolgim zidom sem začutila srce kozmopolitskosti, odprtosti Ljubljane, in bolj ko je bilo ekscentrično ali novo, vznemirljivejše in bolj navdihujoče se mi je zdelo. Zanimivejši pa so bili tudi sama stavba in njena preteklost, njeno življenje in ljudje. Preprosto zato, ker si dober delež ljudi ni želel delavnic in moccachinov, temveč več pomenljivih, recimo temu presenečenj, nepričakovanih spinozističnih srečanj materije, ki se zvedavo obrača po planetu in išče svoj Angry Inch*. To je bil Rog.
Prvi del podlistka lahko preberete na tej povezavi.
Da pa bi ta Rog bolje razumeli, se vrnimo v čas njegove primarne izgube: leta 1994 je znamenita tovarna koles nehala proizvajati ropot in trušč, stroji in glasovi delavcev so utihnili. Izza tovarniških vrat se ni več zapeljalo nobeno kolo znamke Rog, kakršna so prinašala radost vsakomur v kolesju socialistične družbe – od mojstrov, ki so jih izdelovali, do ljudi, ki so imeli srečo, da so si ta kolesa lahko privoščili. A delavnice so se med tranzicijo zaprle, začeli pa so se stečaj, brezposelnost, (pre)kupčevanje, lizingi in špekulacije. A stavba je o(b)stala – velika in prazna, vkopana na zemljišču ob reki, okopana v rumeni svetlobi, kar nekaj poletij in jeseni, dremajoča v sivih zimskih nočeh kot slana rezina (post)socialistične trpežnosti, ki se neskončno ponavlja med prihajajočimi in odhajajočimi časi.
To je trajalo vse do tistega dne leta 2006, ko je skupina arhitektov, aktivistov in umetnikov odprla vrata, očistila prah in vrnila življenje v kraj, ki so ga oblasti in vsakokratni lastniki pustili propadati. Zapuščena tovarna Rog je postala Avtonomna tovarna Rog (AT Rog) in je ponovno oživela v neko novo življenje. Na dvorišču stare tovarne so trčili svetovi političnih aktivistov, glasbenikov, pesnikov, cirkuških in drugih popotnikov z vseh vetrov. Rodila so se politična gibanja, ki so spremenila potek življenja marginaliziranih ljudi: Protirasistična fronta brez meja, samoorganizirani Izbrisani, ambulanta Zdravnikov za azilante, Gmajna, Nevidni delavci sveta, Ambasada Rog ter razne transnacionalne, politične, športne, delavske, migrantske in feministične skupine. AT Rog je ponujal nekaj, česar denar ne more kupiti in noben zakon ne more predpisati: material, ljudi, politiko od spodaj, potencial. Kot prostor je bil toliko nepredvidljiv, kot je bil predvidljiv, včasih tudi prazen, v drugih primerih pa razburljiv. Vsekakor je bil kakofoničen. Od večerij za lačne, zatočišča za razseljene do transnacionalnih obiskovalcev, neodvisnih razstav in brbotajoče, še kako konfliktne politične energije – AT Rog je dajal, je pa tudi jemal. Vzel je trud, leta življenja, zdravja, denarja in živcev. A kaj, ko je onkraj dajanja in jemanja nosil tiho vrednost, ki je ni mogoče ovrednotiti oziroma reducirati na materialne, merljive ali utilitaristične pogoje. AT Rog je bil prostor, ki je s časom postal veliko več kot le to – postal je ideja.
»Stara tovarna št. 72« je bila z vsem svojim žalostnim nasiljem in strupeno umazanijo predvsem prostor politike, torej skrbi in ustvarjalnosti, konfliktov in soočenj; a tudi prostor cele vrste »prvih« doživetij: prvih performansov, prvih bralnih krožkov in branj poezije, prvih ljubezni, prvih pretepov, prvih soočanj z marginalizacijo, prvih stikov z realnostjo življenja in smrti – in to v veliko širših razsežnostih, kot jih Ljubljana lahko ponudi svojim prebivalcem (Neljubljančanom, pa tudi Ljubljančanom). Tja je lahko povsem po naključju sredi noči prispela neka Francozinja, ki je spremenila okolje, ostala nekaj časa in nato odšla. Zatem Pakistanec. Zatem Afganistanec. Nato so se lahko spontano tam ustavili italijanski sindikalisti, prespali, pustili kaj za seboj … svet je prihajal v Slovenijo, brez denarja, projektov, papirjev in zapletov. Hodil je skozi Rog, in kdor je želel, se je lahko vanj vpel, njegove možnosti zunaj cone udobja so se povečale. Svet je prihajal v Rog in presenečal. Skratka, utopično mesto so v bistvu utopični ljudje, ki si/se dogajajo. To utopično pa ne obstaja kot monolit, saj obstaja samo proces, ki melje in ustvarja. Gre za minevanje, v katero smo s svojim življenjem vpleteni tukaj in zdaj. Ta tukaj in zdaj je sedanjost, vsakokratna možnost misliti tisto, kar bi lahko bilo (dostopna stanovanja in dostojanstvo za vse) in kar je nekoč bilo (tramvaj), ne zna pa morda misliti samo sebe. Za to potrebuje distanco – pogled z roba. In distanca do neoliberalizirane Ljubljane je prihajala iz Roga, z roba Roga, ki je bil tudi sam na robu.
Mesto je zgrajeno iz odnosov med svojimi prostorskimi merami in dogodki znotraj njih.
Zvok rešilnega avtomobila. Številni pogledi, ki sledijo vsaki leteči, padajoči in razdrobljeni opeki. V zrak frčijo knjige, mačke, tudi rože, ki sem jih jeseni presadila. Spet bagri, spet Dolinšek in nezaščiteni delavci, ki z golimi rokami mečejo azbestno streho na tla. Prah leti na vse strani.
Hkrati, ko so mestne oblasti rušile en zid, so postavile druge nevidne zidove in ograje. Ta zdaj sterilna in odmevajoča stavba niti v devetdesetih letih ali med krizo na svojih tleh ni imela tako avtoritarnih ljudi kot tistega januarja, ko je že drugič postala predmet izgube. Uničujočih potresov ni doživela, samo rušitev. Travma je zato v primeru Roga drugačna – je travma privilegija in pohlepa. Nekako tako kot številne druge tovarne je bil tudi Rog zapuščen kot tovarna, ki je ljudem dajala delo, od takrat pa je bila večina skupnih, občinskih in javnih prostorov v mestu požrta v debelo mošnjo zasebne lastnine. Ta neusmiljeni cunami privatizacije in njegovo najnovejše valovanje sta opustošila AT Rog. Njegova lastnica – občina – je v postopku delovala kot nevidna lutkarica, ki se je malo poigrala s svojimi marionetami, in kot prave lutke, te uniforme niso spregovorile. Niso imele volje za poslušanje niti za razmišljanje. Imele so pač službo. Niso imele sodne odredbe za rušenje. So pa služile. Prav tako niso imele sodne odredbe za razselitev. Po izselitvi ljudi so se s predmeti poslužile.
Rušenje in ruinacija sta sicer procesa, ki označujeta prelom starega z novim. Raziskovalka, aktivistka in pisateljica Emina Bužinkić iz Transbalkanske solidarnosti** je dan po evikciji AT Rog objavila zapis iz svojega dnevnika Življenje po potresu …, nanašajoč se na potres, ki je dodobra pretresel in uničil Petrinjo. Pisala je o življenju kot delu rekonstrukcije. Čeprav dogodek, ki se je zgodil v Ljubljani v zgodnjih jutranjih urah v torek, 19. januarja 2021, ni pretresel zemlje, kot je to storil uničujoči potres v Petrinji, bi ga lahko šteli za poskus pretresanja temeljev solidarnosti in skrbi, grajene in utrjevane več kot 15 let. Iz ruševin v prah – oblasti so poskusile nekaj pokopati, a niso vedele, da gre za seme. Čas se v resnici ni ustavil. Pravzaprav se je razširil v nedoločno prihodnost, ki bo živela, dokler bo živela sama ideja. Ideje ne moreš porušiti z nekaj stroji, ne z mačetami, bodečo žico ali pestmi. Ni je mogoče pokopati, zapreti, izbrisati ali uničiti. In kakopak – nič ni močnejše od ideje, katere čas je prišel. Pred prostori alternativne političnosti v Ljubljani se je znašel izziv rekonstrukcije – ponovne konsolidacije in obnove. V odgovor tistim, ki z Metelkovo v mislih trdijo, da »alternativne prostore že imamo«: ti prostori so že zdavnaj kurirani in spakirani v turistično izkaznico pravljičnega najlepšega mesta. Enačiti ali zamešati možnosti z alternativo pa je tudi rahlo smešno – alternativa je izbira med enim ali drugim, kot taka je zgolj iluzija svobode. Možnost pa ni alternativa. Je neuhojena pot. Možnosti je lahko neskončno. Najdemo jih v prazninah, tišinah, zamujenem ritmu, fragmentih, mimikah. Naključnih srečanjih. Možnost je lahko napaka, glitch, guba v času in prostoru, lahko je en Rog in v njem vse tri, pet ali še več bodočih generacij aktivistov. In ne Janković ne katerikoli drug župan, ne svetnik ne bager takega mesta ne morejo zgraditi. To mesto ne more biti Acropolis in ne Necropolis. Je luknja v pločniku. Je mesto Obljuba.
To neopisljivo domačnost sem doživela pri naključnih srečanjih v Rogu. In to neponovljivo sproščenost je najti ravno v tem, ko na sončen dan spontano zakorakaš v Rog in greš iskat Gala ali kavo, ker je to včasih isto. In nič ni treba, da se zgodi. To je bila ta lepota Roga: da človeku nič ni bilo treba, lahko pa je vse.
Da je bil edini plac, kamor je lahko prišel migrant iz Juge ali iz kake druge tuge in na enem kupu dobil žive odnose, srečanja, žive ljudi, ki delujejo za skupni interes in s srcem, nikakor ne za lasten žep, kajti vsakič, ko je kdo to poskušal, se je vedno slabo končalo. Skratka, opciji, »ali si bogat ali pa reven«, ter pričakovani izbiri, da bomo vsi bogati (ali revni), so rogovci dodali novo možnost: da bi bilo življenje čim bolj brezplačno. Mimoidoči so tam lahko brezplačno počeli vse žive stvari. Ali pa nič. Lahko so se urili in postali tudi socialni delavci, aktivisti, glasbeniki, popravljavci koles. Ali pa nič od tega. So se pa naučili reševati konflikte in pridobili življenjsko znanje, recimo temu modrost. Bolje jim je bilo v Rogu, kot če bi to delili pri kakšnem vodenem krožku ali na delavnici ali tečaju. Zakaj? Ker gre za spontanost realne življenjske vsakdanjosti in ne za vrtiček – konjiček, obšolsko dejavnost ali »projekt« za CV. In ta mimoidoči migrant, tako kot tudi študent, brezposelni, dijak ali kdorkoli, ki bi si to zaželel, si je lahko izbral eno ali več možnosti za drugačno ali povsem novo življenje . V tej tovarni si je vsako možnost lahko izbral sam in jo brez težav svobodno opustil ali spremenil v kaj drugega. Predvsem pa je naletel na naključja, ki jih ni mogel predvideti, niti pričakovati, in ravno ta so pripeljala najširša obzorja v našo slovensko vas.
In kaj imamo zdaj?
Do zdaj je bilo veliko povedanega. Ure in ure gradiva so v arhivih. In veliko velikih in malih imen je povedalo marsikaj o Rogu. V glavnem je bil prostor nasprotovanja logiki, s katero opredeljujemo svoj že tako kratek čas na Zemlji skozi prizmo tekmovanj, nagrad, predmetov, ki si jih lastimo, aplavzov ali ničel na računih. To je ista logika, ki človeška življenja spreminja v številke in statistiko, znotraj katere pomenijo bolj malo. Slovenija ima sicer srečo, da je v njej življenje nekoliko več vredno kot drugje, kjer človeka umorijo za deset dolarjev, a surovejše okolje ko proizvajamo, laže se ta vrednost življenja spremeni. Število in načini umorov ter napadov zoper telo in dostojanstvo na starejše in vse mlajše ljudi kažejo, da se je to zmanjševanje vrednosti že začelo. Pri takšnem napredku je pričakovati, da bo življenje vse manj vredno, razen življenja tistih, ki so pri vrhu ali koritu, ali tistih, ki vestno plezajo v to smer. In žal premnogi marljivi, vestni in naivni delavci vsak dan dokazujejo bogu in svetu, da so vredni svojega življenja. A še najmanj smisla ima lastno vrednost življenja na tem planetu dokazovati na popolnoma napačne načine, pod napačnimi predpostavkami in popolnoma napačnim ljudem. In res, če vprašate številne ljudi, ki ne sodijo v kasto, ki z lahkoto služi denar z nagonskim množičnim butičnim turizmom, bodo rekli: občina bi morala vzdrževati AT Rog in ga pustiti odprtega za generacije ljudi, ki naj bi prihajale in odhajale. Umetniki bodo rekli: potrebujemo bela platna in prazne hangarje. Aktivisti bodo rekli: potrebujemo komunizem in refleksijo. Utrujeni bodo rekli: potrebujemo počitek. Starejši bodo povedali: potrebujemo druženje z mladimi generacijami, ne pa odrinjenost na rob in v pozabo. Mladi bodo rekli: ne potrebujemo starih, potrebujemo prostor, ki je prost, za brezplačno druženje, poskušanje, neuspeh in nove poskuse. A pustimo zdaj vse to. Pričakovati je, da se bo mestnim oblastem zgodilo isto, kot se je zgodilo tudi rogovcem. Prišel bo čas za neke nove ideje in ljudi. Vedno znova je tako: ljudje si zamišljamo nekaj »genialnega« ali mogočnega in se ukvarjamo s tem, a vendarle … še preden končamo, se okoliščine tako spremenijo, da rezultat dela nikakor ne bo tisto, kar smo želeli ustvariti. Najlepša mesta tako postanejo grda, fiktivna bitja, žalostne tavajoče pošasti, emblemi distopije. Morda si želijo »novega« centra Rog, a dobijo fino kurirano čistunstvo. Avtonomni Rog pa bo kot ideja obstal, čeprav bo tudi njegovo ime zelo kmalu, z novimi generacijami, pozabljeno. A v zgodovini se mu bo pripisalo nekaj čudovitega: v nasprotju z novimi in obnovljenimi stavbami, v katerih odmeva, se je v AT Rog izmenjalo kar nekaj »umazanih« generacij in vsaka se je borila zanj. Kdo pa se bo boril za sterilni prostor predragih tortic?
Za konec sledi preprosta avtoetnografija neštetih noči, popoldnevov, ranih zor in brezčasnih trenutkov, preživetih v kromiranih in azbestnih kotičkih stare tovarne. Takšna mesta in trenutki so še vedno zaznavni samo v fragmentih, so skoraj nevidni – in jaz z njimi.
… Neko (no)č sem videl neko takšno »mesto v mestu«. Tovarna sredi hipertovarne. Porušili sta jo vreča denarja in pohlep brez obljube. A pod z bagrom razrahljano plast zemlje je odteklo vse tisto, kar pomeni nekaj več: gejzir perspektiv, ki je prijateljstva nesel vse tja do Savca.
… Nekoč sem slišala za neko mesto, kjer so meščani ljudje z vsega sveta. Nihče ni govoril jezika drugega. In ti meščani so se o skupnem dogovarjali, kot se piše glasba. Nekega deževnega popoldneva sem to tudi našla: slišala sem dvajset violin, kako se uglašujejo. Začele so s škripanjem, potem so se nekaj časa spogledovale, poigravale so se druga z drugo, dokler niso z rahlimi premiki pristale pri skupnem tonu. Zjokala sem se. Prvič sem videla, kako se rojeva glasba, soglasje, sozvočje.
… Nekoč sem zaslutil mesto, ki je lebdelo v zraku. Ljudje so samo prihajali in odhajali. Lepo je bilo gledati, kako je v najbolj tranzitnem medmejnem prostoru vsem nam skupno to, da smo popotniki. Vse, kar lahko, je le to, da si zaželiš srečno pot.
… Nekoč sem sledila glagolici in prišla do mesta, ki je sijalo pod soncem, na betonu, s senco nekih vrb ali brez, pa še ena češnja je bila. Morda je bilo to najmanjše mesto na svetu. Mesto besed, dreves in drznih dvestotih prebivalcev.
Bila sem tudi v mestu, ki se je vseskozi premikalo. Nisi vedel, ali migrirajo ljudje znotraj njega ali mesto samo. Nisi vedel, koliko ljudi je zares tam. Nisi razumela, ali je mesto Veliko ali Majhno. Vsi so se srečevali in si podajali kruh za na pot. In nikoli nisi vedel, ali si odšel iz tega mesta ali prihajaš nazaj pod njegove oboke. Tako premično je bilo vse in jaz … bila sem tako negiben, da se nisem nehal pretakati.
Veliko smo izgubili, medtem ko smo živeli. Izgubili smo drage ljudi, pa tudi mesto, kot smo ga nekoč poznali. In vsakokratno mesto, ki bo nastalo na ruševinah ali v marmorju, bo z vsemi svojimi možnostmi še vedno vodilno ne le pri »razvoju«, hiperkapitalizmu, vojni – kakorkoli – temveč tudi pri uporu in ustvarjalnosti. Toda ona je malo luda, ne moreš je napovedati.